
A strategy for identity management that provides people authority over their own data is known as decentralized identification, sometimes known as self-sovereign identity. It is a notion that, in the future, virtually surely will contribute to digital identity.
Some fundamental beliefs about how internet identification operates are called into question by decentralized identity (DID). In specifically, the notion that the delicate data that makes up identification must be managed by a third-party authority. With potential benefits for privacy and accessibility, DID offers up the possibility of minimizing reliance on such authorities and giving the data’s owner some measure of autonomy.
People can manage their own digital identities independently of a particular service provider thanks to a sort of identity management known as decentralized identity.
A digital identity is the collection of data online about a person, business, or piece of technology. A digital identity is composed of the following data:
- User names and passwords
- Search history
- Social security number
- Buying history
How companies may profit from decentralized identity?
It enables enterprises to rapidly confirm information without having to get in touch with the providing entity, such a university or agency that issues driver’s licenses, to make sure that IDs, certificates, or papers are legitimate. Traditional, manual verification procedures need a lot of time—weeks or even months—and consume a lot of financial and human resources, slowing down hiring and processing times. Imagine being able to quickly validate someone’s credentials by scanning a QR code or putting them through an easy-to-use application.
It also allows issuing companies to easily give users Verifiable Credentials and stop fraud in a method that significantly lowers costs and boosts efficiency.
How decentralized identity benefits individuals
- The user is able to substantiate their claims independently since they are in complete control of and ownership of their identity and credentials.
- People may choose which details they wish to share with particular entities, such the government or their employment.
- Once a person’s ID is saved in their mobile digital identity wallets, no one can take it away.
- With the aid of user-friendly systems like Dock, people can simply create and manage their decentralized identities.
What Exactly Is Sovereign Self-Sovereign Identity?
Self-Sovereign Identification (SSI), a method of digital identity that provides people control over their digital identities, is a concept that is interchangeably used with the phrase “decentralized identity.” The following are the three pillars of self-sovereign identity:
- Blockchain: A decentralized database that is shared among computers connected to the blockchain network that stores data in a way that makes it extremely difficult to alter, hack, or defraud the system.
- Verifiable Credentials (VCs) are electronic versions of paper-based and digital credentials that are cryptographically secure and may be presented to organizations that require them for verification.
- Decentralized Identifiers (DIDs): Cryptographically verifiable identifiers held only by users, independent of any centralized authority, and produced by users. DIDs don’t include any personally identifying data.
How Decentralized Identity Works
The key components of a decentralized identification system are as follows:
- Blockchain: A decentralized database that is shared among computers connected to the blockchain network that stores data in a way that makes it extremely difficult to alter, hack, or defraud the system.
- Decentralized Identity Wallet: An software that enables users to maintain their Verifiable Credentials and establish their own decentralized IDs.
- Decentralized Identification (DID): A special blockchain identifier composed of a string of letters and digits that includes information such as the public key and verification data.
- Verifiable Credential (VC): A digital version of both paper and digital credentials that has been cryptographically protected and may be presented to organizations that require them for verification. The principal players in the VC system are as follows:
- Holder: A person who creates a decentralized identity via a digital wallet program and obtains a Verifiable Credential as a result.
- The company that issues a Verifiable Credential to the bearer after signing it with their private key is known as the issuer.
- Verifier: A party that examines the credentials and has access to the blockchain’s public DID of the issuer to determine whether the Verifiable Credential that the holder supplied was indeed signed by the DID of the issuer.
What Are Decentralized Identifiers (DIDs)?
A DID (Decentralized Identifier):
- Consists of a string of letters and numbers that is kept on the blockchain, is unrelated to any company, and serves as a globally unique identity.
- Provides a means for proving cryptographic control by the owner.
- Includes one or more pairs of private and public keys
- Does not include personal information or wallet details
- Enables two parties to communicate privately and securely, and it can be confirmed anywhere, at any time.
To allow use cases like sign-in, data encryption, and communication, a DID may be used to locate associated DID documents that contain pertinent information.
Currently, the majority of us access websites, applications, and services by using identifiers like emails, passwords, and user names. However, these identifiers frequently lead to:
- Our personal data being breached
- Identity fraud
- Without our awareness, other parties are receiving our data
- Increasing the difficulty of someone managing all of the logins
- Relying only on service providers, who reserve the right to remove these identifiers at any moment
But many of these issues are resolved by DIDs. They make it possible to exchange and validate digital credentials in accordance with a recognized global standard. A party may create as many DIDs as desired for various partnerships, whether they be individuals or organizations. DIDs resemble the several personalities that one might construct.
Currently, a lot of individuals utilize LinkedIn to display their information and professional expertise. However, they create a second Facebook profile because they don’t want their potential employers to view their personal images and hobbies. Similar to a DID, you may create many profiles for various uses.
You may, for instance, have a DID for:
- Your individual preferences, such as demonstrating your legal age to purchase alcohol or logging onto shopping websites.
- Professional uses when you might present an employer with your DID to demonstrate your educational or professional qualifications.
- Using various cryptocurrency-related applications and services that require identification verification in order to access for trading and investing purposes.
How Do Decentralized Identifiers Get Created?
You can generate a DID by doing the following using a Dock Wallet and Dock Certs:
Log in to Dock Certs after creating an account. Use Test mode if you’re still getting used to the platform.
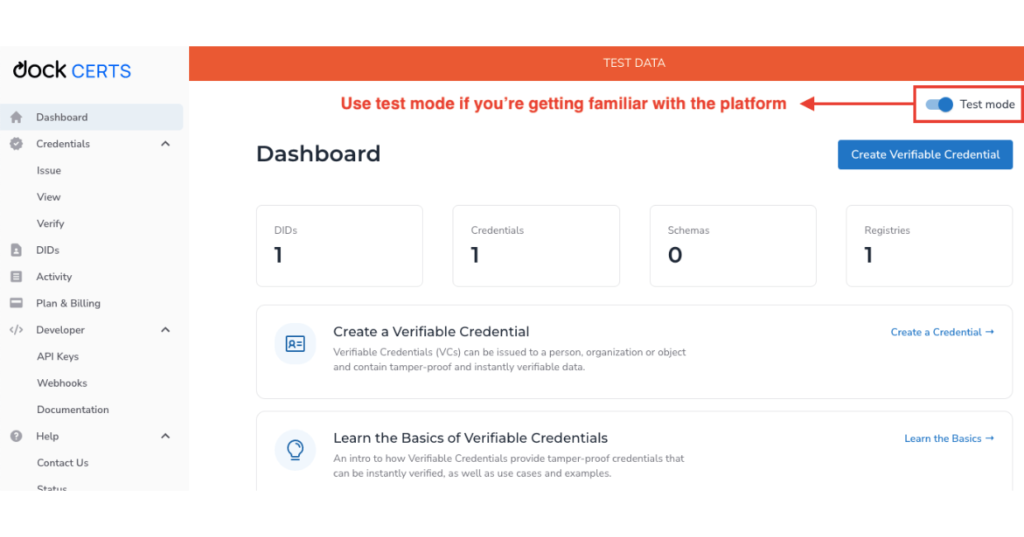
On the upper right, select Create Verifiable Credential.

Create the issuer profile (for a university, as an example), and leave the Key Type as is. Select Create a DID after that.
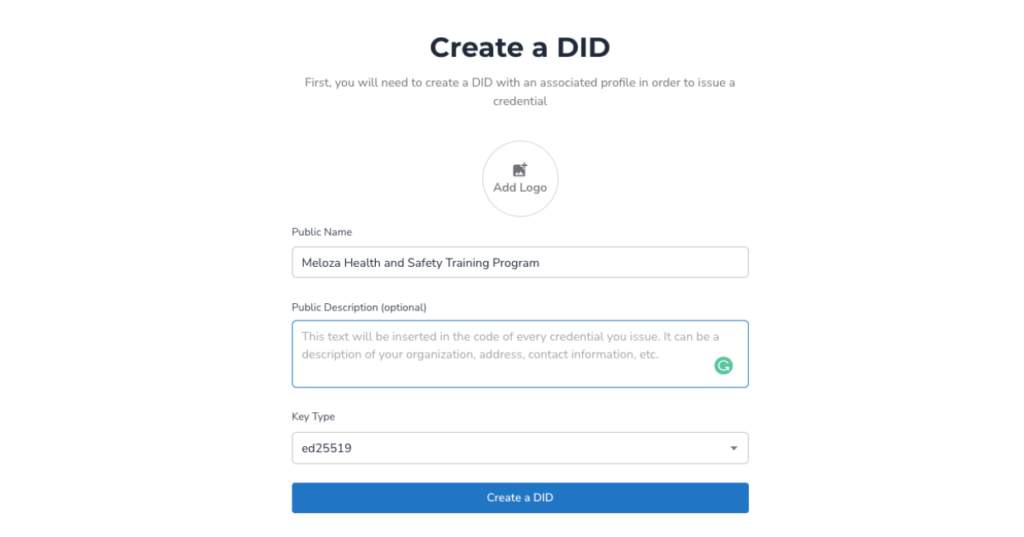
Select the DID from the basic template selections, then click Continue in the top right corner.

Using the Import CSV option, you may manually add credential recipients one at a time or in bulk.

If you manually add a person, you will provide information similar to the example below, in which we are identifying the person by their employee number. Click Add Recipient when you’ve finished filling out all the fields.
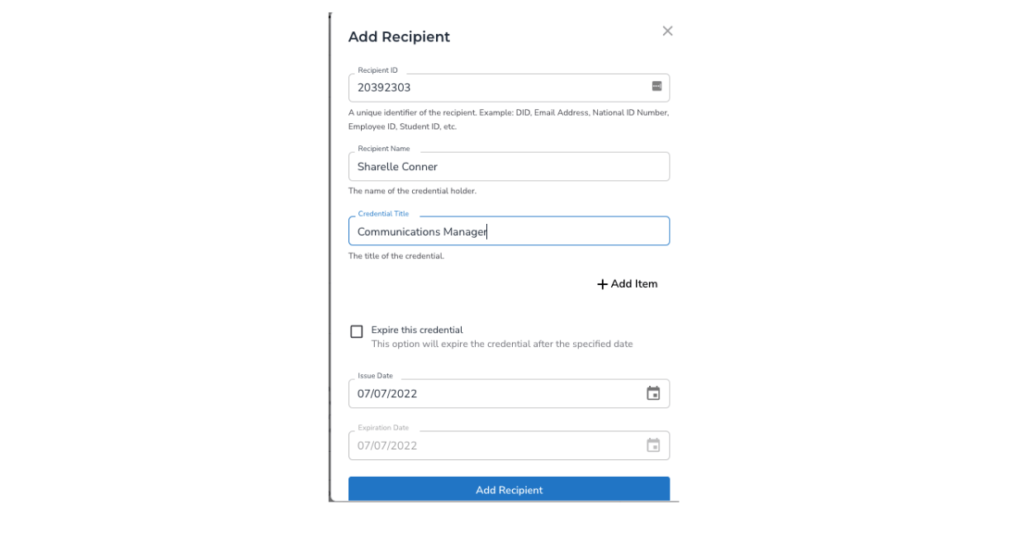
The details will show up as follows:
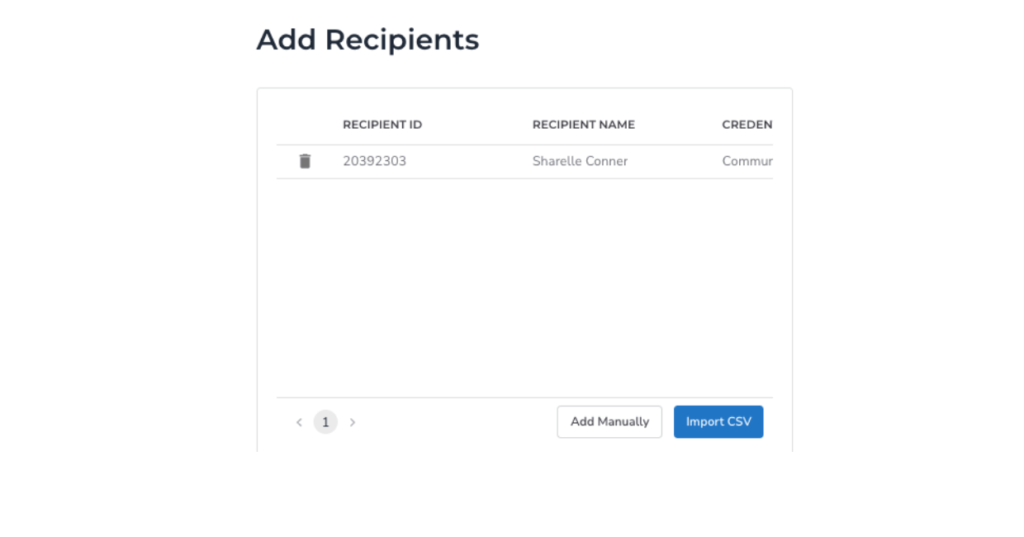
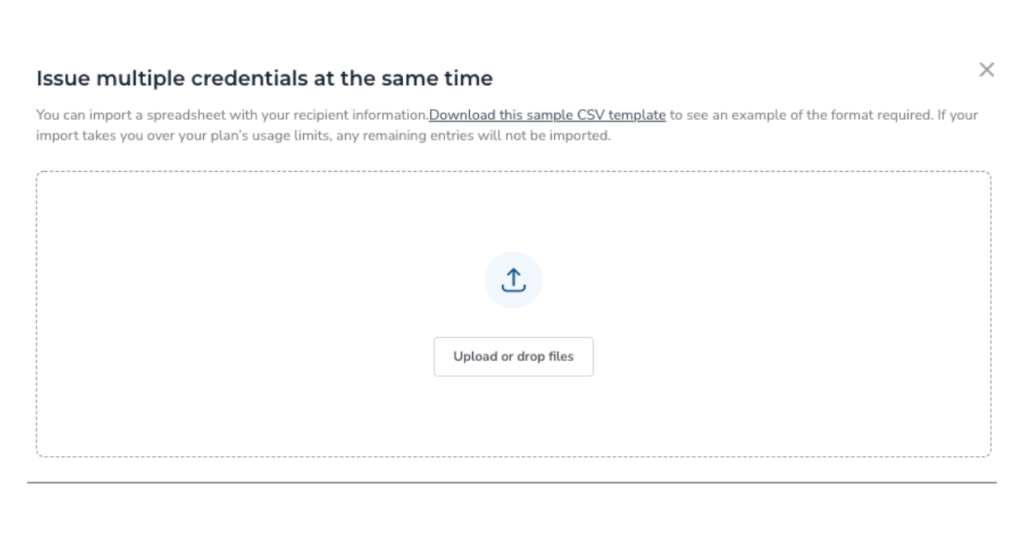
You may also import a CSV file to do mass issuance. Fill out the example template after downloading, then upload it.
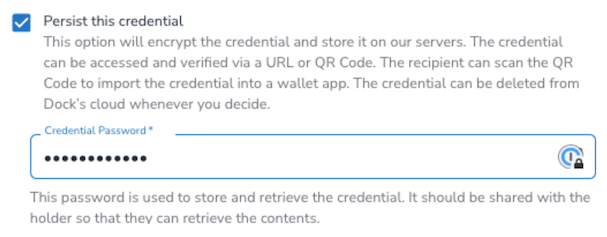
The following choice is to “Persist the Credential,” which instructs Dock to safely keep the Credential on our database (but NOT on the blockchain).
The receiver may just scan the QR code with their Dock Wallet software to import the credential in their wallet if you persist the credential. If you persist the credential, a QR code will appear on the PDF.

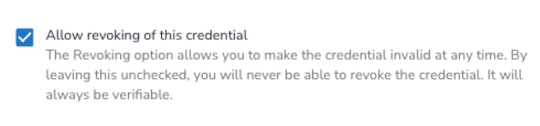
The ability to revoke this credential is possible by adding a registry (record) to the blockchain.
You may add a hash of the credential you issue (like a digital fingerprint) to the Dock blockchain by anchoring the credential. This makes it possible to confirm the creation date and author.
You may then download the credentials in JSON and PDF formats by clicking Issue Credentials in the upper right corner. A JSON file is a file that contains basic data structures and objects in the standard data exchange format known as JavaScript Object Notation (JSON).

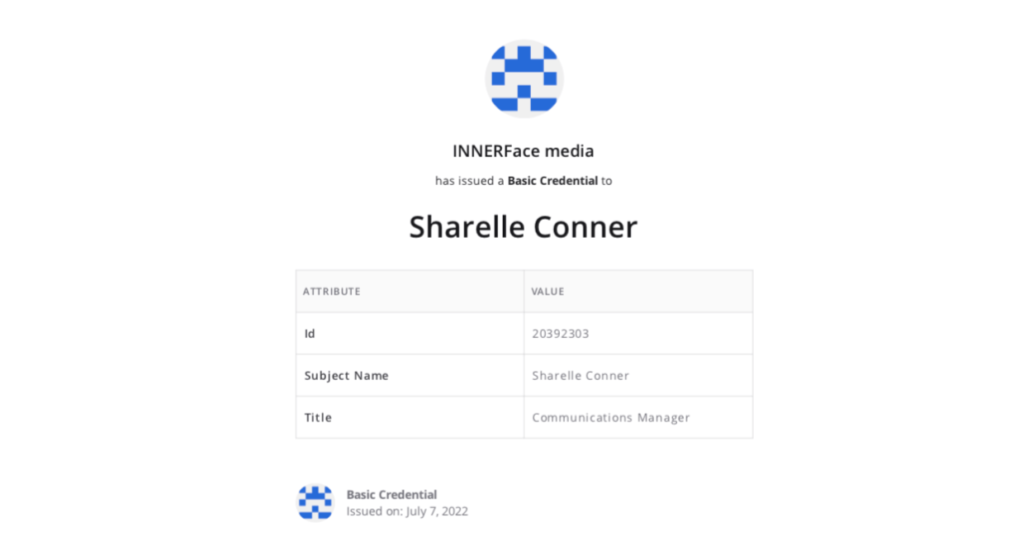
This is how the Basic PDF credential will appear:
It’s critical to understand that you cannot recover a credential if you do not persist it or download it.
The receiver can get the PDF and JSON files through email from the issuer. The Relay Service, which will immediately transfer the credential to the recipient’s wallet, will soon be made available.
The receiver must download and import the JSON file if there isn’t a QR code on the PDF file (since the credential wasn’t persisted). To accomplish this, choose Credentials, choose the JSON file by clicking on the plus symbol in the upper right corner.
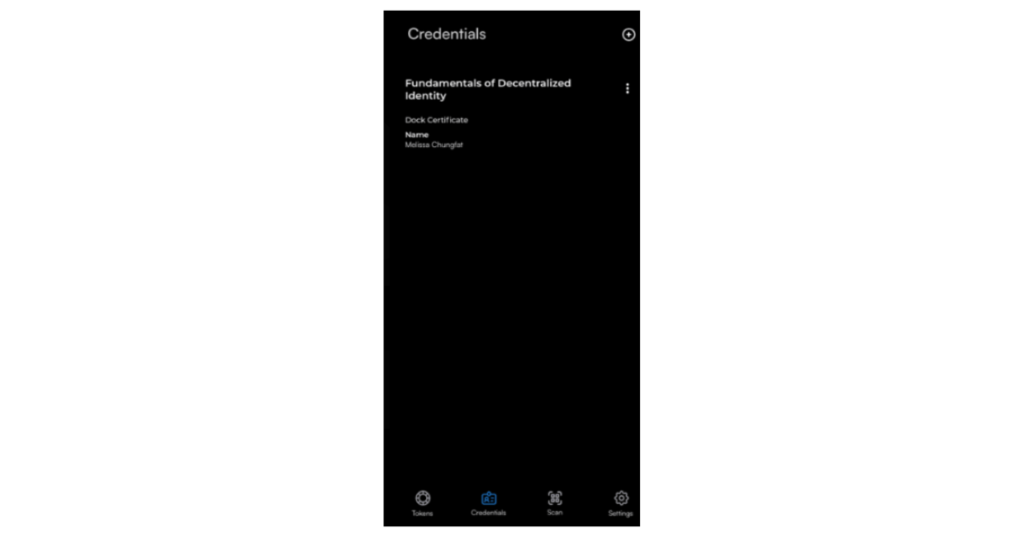
The Dock Wallet will display the credential right away.
With decentralized identification, users may own and maintain their own digital identities independently of a particular service provider. Many of the issues brought on by centralized and federated identity management systems, such as widespread certificate fraud, time-consuming and expensive verification procedures, and the possibility of data breaches, are being resolved by decentralized identity technologies.
























